|
CES is an annual trade show organized by the Consumer Technology Association. Normally held in January in Las Vegas, but held online this year for the first time ever. CES typically hosts presentations of new products and technologies in the consumer electronics industry. It's one of the most important and influential technology conventions in the world. It often features the lastest and greatest technology trends which will impact organizations of all sizes. This presentation will be a round-table discussion with K2 instructors, Randy Johnston, Ward Blatch, and Brian Tankersley. They are long time attendees of CES and attended this year's event from the safety and comfort of their homes. They will discuss their experience with this year's event and the major emerging technologies which made their debut. Tune in to learn the latest and greatest which emerged from this year's CES!
My home office has gone through significant changes from where it started in 2005. Back then, we had a small business server for file and printer sharing and our email server. The risk of downtime and the cost of upgrading resulted in our move to Office 365 for email in 2009. We still maintained our files on network-attached storage with cloud-based back. In 2018 we moved our files to SharePoint online, which has been working great for us the past two years. Updates in 2020 Microsoft Teams has proven to be invaluable to us this year. To ensure we have the best online meeting experience, we upgraded our mics to the Blue yeti and upgraded our webcams to 1080p. Updates Planned for 2021 As part of our annual IT review, I am now looking at what upgrades we need to consider for 2021. Our system worked well through 2020, with only one significant issue. Our PC purchased for the conference room and used for online meetings, webinars, and recording was dramatically underpowered. The following is a summary of each substantial section of our review. Software Our accounting practice will continue to move clients, where applicable, to cloud accounting. The online solutions meet the needs of our clients and simplify operations for both our clients and us. Our write-up and tax software are working well, and with the data stored on SharePoint, we do not see a need to move to cloud solutions for either. Our office runs on Microsoft 365, providing us with Microsoft Office Pro Plus, file sharing and storage, Microsoft Teams, calendar sharing, email, and an online booking site for clients. We have selected the Microsoft 365 E3 subscription to provide improved security, including data loss prevention and restricted access. With the combination of retention policies in SharePoint and Adobe Acrobat Pro DC, we can operate as a paperless office. The team at K2E Canada Inc. moved to LastPass for Teams, providing us with improved passwords and easy sharing to common sites the team uses. The result is no changes are planned for software in 2021. Firewall and Wi-Fi We have been using a PFsense firewall for several years; its advanced configuration options are an excellent fit for our office. A couple of years ago, we migrated our guest wireless system to Nest Wi-Fi. The advantage of this system is the easy setup and configuration with the power of a mesh network. Performance is excellent and a great match to our cable internet connection. With most of our devices not Wi-Fi 6 compatible, there is no need to upgrade. Hardware Scanners We are using Canon ImageFormula scanners and will continue with them for the next couple of years. Laptops With its docking station, detachable keyboard, and digital pen, the Surface Pro is our standard laptop. My Surface Pro 4 has worked well for the past five years, but it will be upgraded in 2021. The need for additional ram and a new processor is evident when compared to the performance of my partner’s Surface Pro 7. The replacement will be the new Surface Pro 8, expected to be released in the first quarter of 2021. The upgrade will be an i7 with 16GB of Ram and 256GB SSD. Desktops Our office desktop computers are a mix of Dell and custom builds. These computers are a mix of different generations of i5 and i7 processors with a minimum of 8GB of ram. The conference room desktop, an i5 with 8GB of ram, has been moved to a workstation and replaced with a seven-year-old custom build. Despite the processor’s age, an i7 4th generation, the system works well because it has 32Gb of ram. With new desktop processors being released in the first half of 2021, we will wait to upgrade this old machine. The upgrade will be either the 11th generation i7 or a Ryzen 5000 series with a minimum of 18GB of ram, reusing the existing SSD, and a dedicated video card such as the Radeon Pro WX 4100. Summary Our IT setup has taken a long time to mature to the point we are at now. The goal has always been to keep the design as straightforward as possible while maintaining high availability, security, and remote access. With just a couple of hardware updates, we should be in good shape for 2021. Ward Blatch, CPA CA
As meeting online has replaced in-person meetings, I have noticed that many people struggle as they don’t have a few essential pieces of tech. The following are my tech recommendations to improve your online meetings. Wired Internet Whenever possible, the use of a wired internet connection is preferable for online meetings. A wired connection will provide consistent performance during the entire session. During a recent meeting with a colleague, their sound and picture kept cutting in and out. The cause was the wifi in their home. Dedicated Mic The mic built into your laptop or webcam may seem perfectly adequate to you. However, others attending the session may not feel the same. Many built-in mics do not provide sufficient directional focus causing significant background noise or, worse yet, feedback from your speakers. I recently upgraded to a Blue Yeti, a great mic with the ability to select the pattern for the mic between stereo, cardioid, omni and bidirectional. For USB mic recommendations, check out PCMag 11 top picks at https://www.pcmag.com/picks/the-best-usb-microphones Another option is a good quality headset with a boom mic. The disadvantage is the discomfort of wearing a headset compared to having a mic sitting on your desk and how you look wearing it. Speakers The important part of any speakers you are using is that the mic is in front of and not facing the speakers. In cases where this is not possible, earbuds are a more discrete option. I use the speakers on my monitor for most meetings; however, when others are around, I use earbuds plugged directly into my Yeti mic. WebCam A camera can range in price significantly, and at this time are very difficult to find. At a minimum, it should be 720p, preferrable 1080p. I have ordered a replacement for my old 720p camera, and when looking at alternatives, I considered using my smartphone or digital SLR camera. Check out webcam reviews and links to using your digital SLR or smartphone at https://www.pcmag.com/picks/how-to-buy-the-best-webcam. Lighting What is a good webcam without good lighting? First, make sure not to have anything bright behind you, which can cause exposure issues. You may also find a room with a brightly painted wall can change the hue of the image. I have such a wall and by pointing an inexpensive LED desk lap at myself, the colours and overall image quality improved. There are dedicated lighting systems for use with your webcam, which will further improve video quality. Check out your favourite tech store for all of the options available. When people in the meeting can see and hear you clearly, the whole online meeting process is better for everyone. Review your tech and invest in some of the above-noted items; after all, online meetings are here to stay. One last thing, don’t forget to clean up the background. Ward Blatch
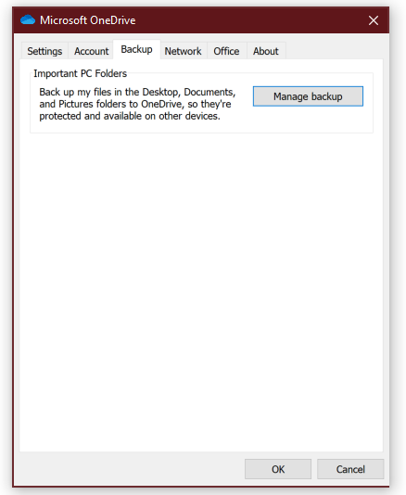
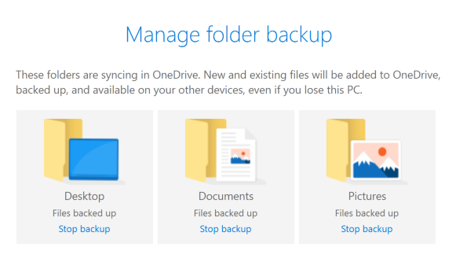
During a recent client visit, the ubiquitous question was asked: "Why would I use SharePoint or Teams instead of OneDrive." These three services from Microsoft all provide file storage, sharing, and collaboration, so it is easy to understand the confusion. Let's look at when each is the right choice. OneDrive for BusinessOneDrive's name is an attempt to note that this is the location for One person, you, to store your files. An option in OneDrive is to backup your essential PC folders, including desktop, documents, and pictures. To turn on the backup feature, go to OneDrive settings > Backup > Manage Backup. In the window that opens, select the folders you will backup to OneDrive. It will be syncing the files providing access from any device and creating automatic versions of data in case you make a mistake or become infected with ransomware. OneDrive is the storage location for your files. Sharing of files is possible with OneDrive, but that is not its primary role. SharePoint SharePoint is for sharing files. It is the equivalent of your network share, providing centralized controls and file access permissions. Providing critical advantages over a file share on the network SharePoint allows for the uncomplicated implementation of data loss prevention and policies to the data. Using the OneDrive app, you can sync a SharePoint document library to your local computer for a simple method to access, save and share files. The files remain in SharePoint and will download when opening. You can mark files that you may need while offline as "Always keep on this device." Microsoft Teams Microsoft Teams uses SharePoint document libraries file storage and therefore has all the benefits of using SharePoint. Additional benefits of Microsoft Teams are the integrated chat, video conferencing, presence awareness, and a simplified interface to providing security over your organization's documents. If you have not started replacing your network file shares with SharePoint, then Teams is the place to move files. It provides the same sync and access to data as SharePoint does with a much easier process to set up and the additional collaboration features. The one cautionary note, at the time of posting, is that Teams does not allow for file sharing to people outside the organization unless they have a Microsoft Account associated with their email address. Summary For efficient and effective file-sharing, use Teams and SharePoint, and for your files OneDrive. Make sure to take advantage of the OneDrive app for syncing and backup of your Desktop, Documents and Pictures folders. Ward Blatch
Are you thinking about upgrading your technology in a small business or startup? Of course you are, because technology is the key to running any size business – including small businesses and startups – successfully. However, you may also be wondering how you can afford new technology, given budgetary constraints – a concern for smaller organizations. Consider this point: technology should be viewed as an investment, not an expense. Further, properly implementing the latest technology into key operations of your business can set your business apart from the competition. Therefore, the investment you make in technology should yield returns many times over the price paid. Following are four ways you can update your technology in a small business and achieve outstanding returns in the process. Overhauling Your Small Business Website With more people searching for businesses online, having an exceptional and efficient website is more important than ever. So, if your website is lacking some luster, you may want to invest to bolster your online presence. For example, hiring a PHP developer can give your business site the edge needed to stand out among the competition. Most sites use PHP code, including those powered by WordPress. Therefore, hiring freelance PHP developers could be the key to ensuring that your small business website is user-friendly. Further, with the right updates you should be able to make future changes on your own. Of course, this means you won’t need to hire a developer each time your site needs to be altered. Freelance job boards make it easy to search for PHP developers who are familiar and comfortable with this technology. However, you should still confirm each candidate’s knowledge of both test suites (https://k2e.fyi/TestSuites) and project management tools (https://k2e.fyi/ProjectTools.) You can also use the links provided to enhance your own knowledge of these essential technology terms. By doing so, you will be better prepared to hire the most qualified PHP developers for your business. Additionally, if you want your project to be completed without a hitch, it’s also important to use those project management tools and lists. Doing so will help to ensure you and your freelance developers are on the same page. Adding or Enhancing E-Commerce Offerings Did you know that some of the simplest technology upgrades can provide the biggest boosts to your small business profits? One such update that every small business owner should consider is adding e-commerce capabilities to their website. Not sure how to get started? We suggest using one of the many e-commerce wikis and resources available online (https://k2e.fyi/ecommerce). These should help to take the stress out of adding online shopping to your small business website. Helpful resources such as these contain valuable information regarding all aspects of getting started with an e-commerce business. Examples of available content include resource management, customer service, brand equity, and effective advertising. Having these trusted resources at your fingertips can make adding or enhancing the e-commerce section of your website much easier. In turn, this will give you a major advantage over other competitors. If you already have a wide selection of e-commerce products and need help moving those items faster, then technology can help you as well. You can have your freelance PHP developer offer helpful website elements. Examples of these include guest checkout capabilities and a streamlined checkout process. Both these additions should help reduce shopping cart abandonment (https://k2e.fyi/shoppingcart). As you convert those abandoned carts into successful checkouts, you should see your profits increase Moreover, you will also be cultivating loyal relationships with new and existing customers. Streamlining Communications and Operations Are you still using two phones to keep your work life and personal life separate? If you upgrade to one of the latest smartphones, you can take advantage of apps (https://k2e.fyi/2ndNumberApps) that allow you to ditch that second phone and use a single device for multiple phone numbers. Apps like Google Voice and TalkU also make it simple to get a new number specifically for your small business. In turn, this can help you maintain some privacy in your personal life and achieve work-life balance. No doubt having a single phone for work and business can keep you from juggling two devices. However, it can also help reduce your business expenses. It’s also crucial that you’re not using an outdated phone. The latest smartphones have the speed and capability you’ll need to handle communications and run your business. If you’re looking to purchase a new model, top phone wireless providers often offer trade-in deals on new models. Once you have a new high-powered phone, you can access leading business apps (https://k2e.fyi/30BestApps), for an added boost in efficiency. Securing Small Business Internet Connections Is your business using a Virtual Private Network (VPN)? If not, then you may want to consider upgrading your internet connections to incorporate this technology (https://k2e.fyi/usingavpn.) By using a VPN to secure your company’s connections, you create an encrypted pathway to the Internet. This will help keep cybercriminals from gaining access to private and confidential information. You can deploy VPNs through subscription-based services or by purchasing a VPN-enabled router. With a few minutes of setup time, you can create your own private internet connection to add a layer of security to your daily business operations and communications. Summary By upgrading the technology that powers your small business, you could help boost your company to the next level of success. Technology has the power to promote growth, increase profits, establish security, and streamline daily operations. However, to be successful, you need to know which upgrades to focus on first. Setting up a VPN or adding e-commerce capabilities can be almost effortless changes. Likewise, addressing communications needs and upgrading your website can yield almost instant results. Further, each of these enhancements have the power to distinguish your business as a leader in your field, boosting ROI in the process. So, keep this technology guide handy, so that you will know which technology updates and investments make the most sense for the success of your business. Randy Johnston
How do you protect yourself against phishing attacks? You have probably heard about phishing in the context of the Internet. But in fact, phishing is older than the web itself. This password-stealing technique was first used over the phone. Hence the name that’s a portmanteau of “phone” and “fishing”, as in fishing for passwords or other information. Today, phishing attacks are still going strong, although now in digital form. Read to find out what a phishing attack is and how to protect your accounts from this common cyber threat. How Does Phishing Work? Phishing is a game of deception. A phishing attack involves hackers sending emails posing as a legitimate institutions. The purpose is to trick victims into revealing sensitive information, such as passwords or credit card details. Phishing emails use manipulation to compel victims to reveal their information. They often convey a sense of urgency, informing the target that they’re in an overdraft or that their credit card has been blocked. Alternatively, phishing emails would describe too-good-to-be-true scenarios, such as winning a contest the victim never entered or getting an unusually high tax refund. Typically, phishing emails contain a link that will redirect the victim to a website. These websites attempt to replicate the sites the hackers are impersonating. The unsuspecting target will be prompted to enter their login details or card details as usual. Unfortunately, this information will then go straight to the hackers who can now take over accounts or perform banking operations in the victim’s name. In an alternative version of phishing, the link won’t take the victim to a site. Instead, it will download malware onto their computer instead. That malicious software will then provide a backdoor to cyber criminals to take control over the device or steal sensitive information. How to Protect Yourself and Your Data Know How to Spot a Phishing Attack The first step to protecting yourself from a phishing attack is to be aware of their existence and treat all incoming emails with a healthy dose of skepticism. Beware of emails that ask you to reveal your personal data and never click any links in suspicious emails. If you get an email from your bank, the government, or PayPal asking you to log into your account, don’t follow the links in that email. Instead, search the relevant website in your search engine and log in that way. If you want to be extra sure, it’s a good idea to bookmark your bank’s and other important institution’s websites for future reference. Look also for warning signs in the email. Does it look different than normal? Is the greeting generic and doesn’t include your name? Is the email address correct? Phishing emails are often sent from email addresses that are very similar to the actual ones but so can be easily mistaken at first glance. Set up Two-factor or Multi-factor Authentication (MFA) No matter how careful you are, you might still fall victim to a phishing attack. Cybercriminals who run these schemes are experienced and employ increasingly advanced techniques. The only action that can truly protect you from the consequences of a phishing attack is securing your accounts with two-factor or multi-factor authentication. Two-factor authentication adds another layer of security on top of a password. It combines something you know (password) with something you have (security key, your phone). This means that the hacker can’t simply log in from a new device just by knowing your password. They will still need to complete the second authentication step, which in most cases will be impossible. There are various methods of authentication that can be used as the second verification step. It’s worth noting that using an authentication app on your phone or a hardware security key are preferred forms of verification. Hackers have been known to redirect text messages of the victim to a different SIM card, so using texts as verification is generally discouraged by security experts. Conclusion Phishing attacks can outsmart even extra careful Internet users. It’s important to know how to recognize, what to do when you become a target, and how to prepare a safety net in case you fall for one. In 2019, taking care of one’s cybersecurity is more difficult and more important than ever. You can learn more here in an article on security essentials. Randy Johnston
In the article Your Pa$$word Doesn't Matter the author Alex Weinert says “ – your password, in the case of breach, just doesn’t matter – unless it’s longer than 12 characters and has never been used before – which means it was generated by a password manager”. The article goes on to note “your account is more than 99.9% less likely to be compromised if you use MFA”. This introduces a clear ethical issue for anyone not using a password manager and MFA (multi-factor authentication). Consider the following questions in relation to the five fundamental principles of ethics: Professional BehaviourAre the steps you take to protect the information entrusted to you an indicator of your professional behaviour? Integrity and Due Care Do you have an ethical requirement to take the necessary steps to ensure the integrity and Due Care of data? Professional Competence Do you have the professional competence to implement security over your organizations data? Confidentiality Is your organization maintaining the confidentiality of data? Objectivity Is your organization able to remain objective when assessing the risks of a data breach?
As you answer the questions consider if a competent and objective outsider may be needed by your organization to properly assess the risks and aid with the policy and procedural changes required. As we apply the five fundamental principles of Ethics it will become clear to some that using password managers and MFA is an ethical requirement. For others they do not see a password manager and MFA as an ethical requirement. Opinions on what is ethical behaviour and was is not is often diverse. If your organization is not using password managers and MFA hopefully this will start the conversation. As the end of support for Windows 7 draws closer a quick review of Windows 10 Keyboard shortcuts and virtual desktops is in order.
Virtual Desktops
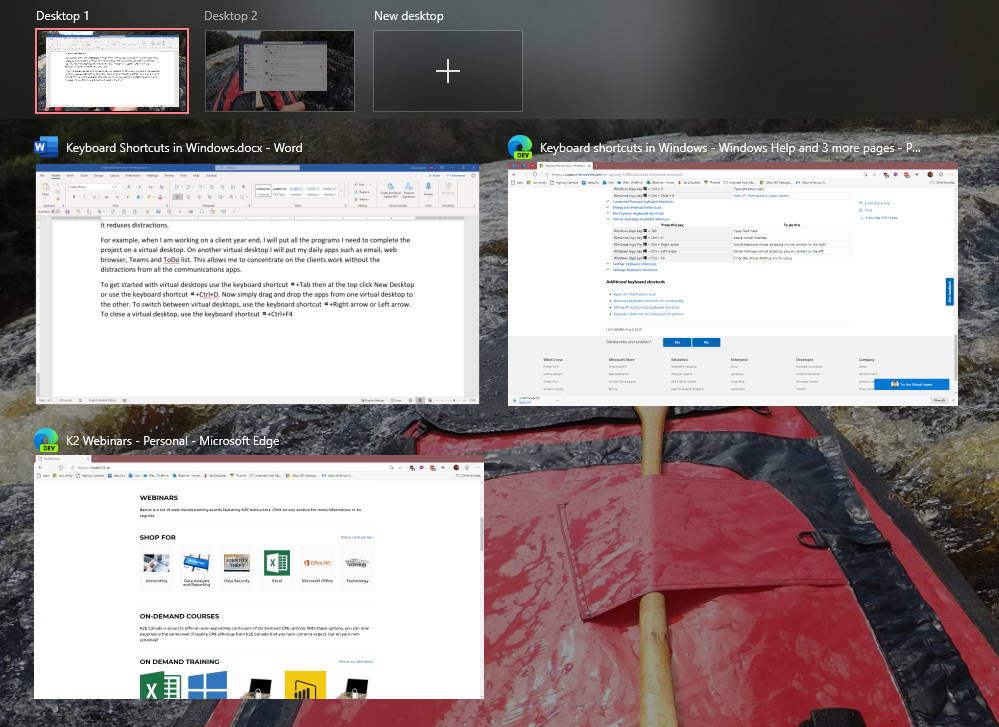
Windows 10 virtual desktops provides a simple to use interface to group applications based on a task, a function, or whatever makes sense to you. By putting apps common to a function on one virtual desktop it reduces distractions.
For example, when I am working on a client year end, I will put all the programs I need to complete the project on a virtual desktop. On another virtual desktop I will put my daily apps such as email, web browser, Teams and ToDo list. This allows me to concentrate on the client's work without the distractions from all the communications apps.
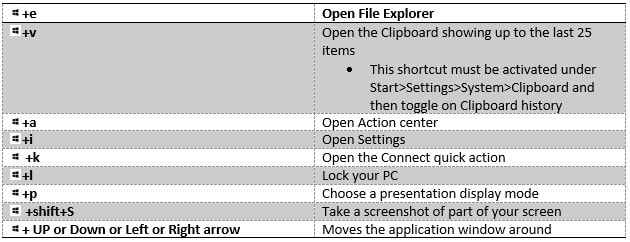
To get started with virtual desktops use the keyboard shortcut Windows logo key (WLK)+Tab then at the top click New Desktop or use the keyboard shortcut WLK+Ctrl+D. Now simply drag and drop the apps from one virtual desktop to the other. To switch between virtual desktops, use the keyboard shortcut WLK+Right arrow or Left arrow. To close a virtual desktop, use the keyboard shortcut WLK+Ctrl+F4.
|
Categories
All
Authors
|


 RSS Feed
RSS Feed